Most certificates are issued with a set of purpose which allow to limit certificate usage. If you are planning to use an SSL certificate for encryption, you need to check your certificate purposes extension. Imagine that you are planning to create a web service that use SSL/TLS client authentication. This would be very helpful to avoid attack from outsources. At this step, you should create two type of certificates which should have different extensions like Server and Client authentication.
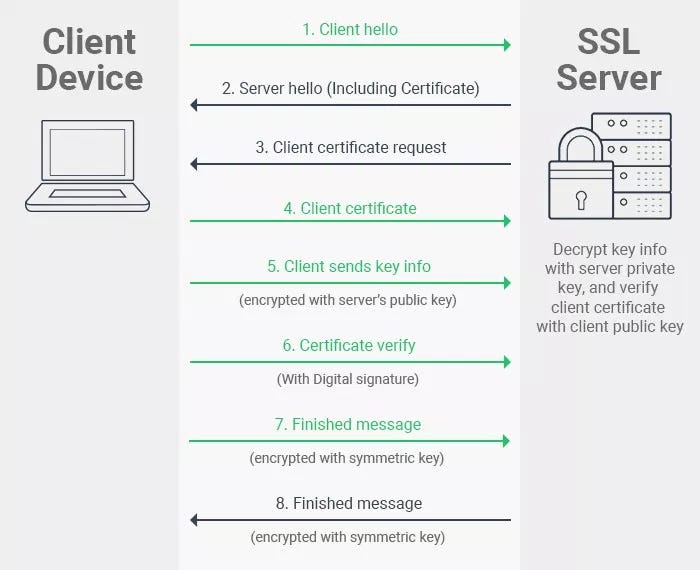
I added a basic script to check certificate purposes extension with OpenSSL command.
#!/bin/bash
host=$1
verify=$2
openssl s_client -showcerts -verify $verify -connect $host:443 < /dev/null | awk '/BEGIN/,/END/{ if(/BEGIN/){a++}; out="certout"a".pem"; print >out}'
openssl x509 -noout -text -purpose -in certout1.crt
openssl x509 -noout -text -purpose -in certout2.crt
######How to run script###########
# bash test.sh google.com 3
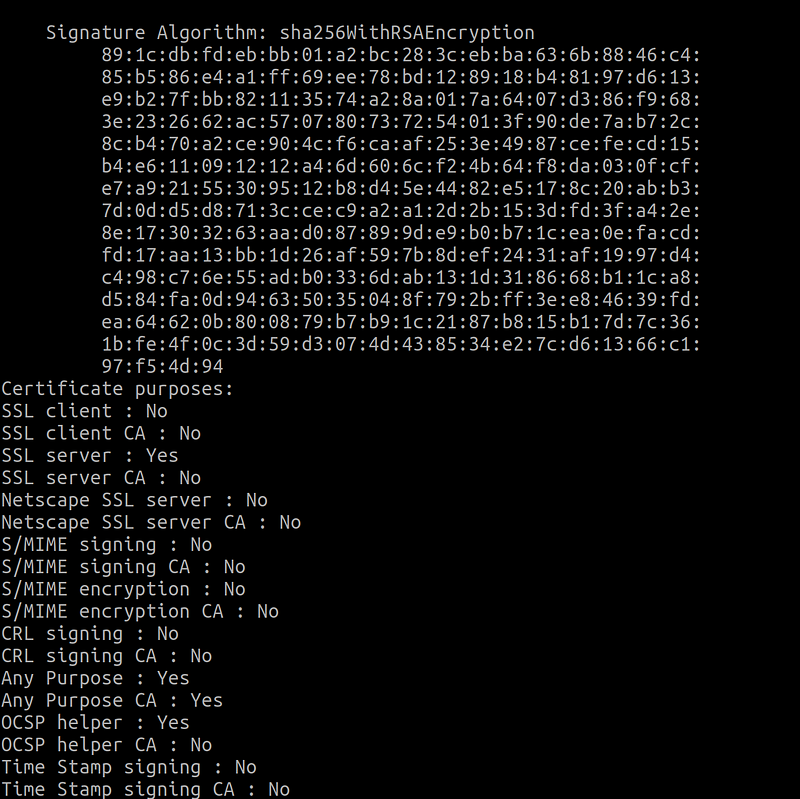
I strongly advice to use OpenSSL to manage and create SSL certificate. It is easy to use and also well documented OpenSource project.
Basically, I described how to change SSL certificates’ purpose extension from “any purpose” to “ client authentication” . You can check these steps to create a certificate that will be used only for client authentication.
Step 1: Configure openssl.cnf file
##Add this lines to the openssl.cnf file## [ usr_cert ] basicConstraints = CA:FALSE nsCertType = client keyUsage = digitalSignature, keyEncipherment extendedKeyUsage = clientAuth nsComment = "OpenSSL Certificate for SSL Client"
Step 2: Use openssl.cnf file to create client certificate
##Windows## set OPENSSL_CONF=openssl.cnf ##Linux### export OPENSSL_CONF=openssl.cnf ##Windows or Linux## openssl x509 -req -days 760 -in Client.csr -CA RootCA.crt -CAkey RootCA.pem -CAcreateserial -out Client.crt -extfile openssl.cnf -extensions usr_cert -sha256
If you are excited to read more please check related posts.


