In this post, I will give a brief introduction to OpenShift Software Defined Network (SDN) concept. Basically anyone with OpenShift background might be interested in this post.
SDN encompasses several types of technologies like including functional separation, network virtualization and automation which focus on enabling the network control to become directly programmable. OpenShift uses SDN approach to provide an architecture that enables communication between pods across the OpenShift Container Platform cluster. SDN comprises three layers;
· Application layer
· Control layer
· Infrastructure layer
These three SDNs’ layers communicate using Northbound and Southbound APIs between them.

Control Layer:
· Centralized view of the network.
· How packets should flow through the network
Application Layer:
· Network applications or functions organizations use (Firewall, Load Balance etc.)
Infrastructure Devices:
· Physical device in network. (Switch devices etc.)
OpenShift SDN plug-ins for configuring the pod Network:
· ovs-subnet: Provide a “flat” pod network for communication between pods.
· ovs-multitenant: Provide project level isolation between pods and services. Each project has a unique Virtual Network ID that identifies pods and service level rights.
· ovs-networkpolicy: Create and configure own network isolation policies.
OpenShift SDN Networks
In the default configuration, the cluster network is the 10.128.0.0/14 network and nodes are allocated /23 subnets. OpenShift needs to have two different network CIDRs which are the Pod Network, and Services Network.
Pod Network variable can be defined with “osm_cluster_network_cidr” ansible host file variable. This variable will determine the maximum number of Pod IPs for the cluster. Default (10.128.0.0/14) value will provide 262,142 IPs for the cluster. If you need to configure Pod network, follow official documentation for more detail.
Service Network variable can be defined with “openshift_portal_net” ansible host file variable. Default (172.30.0.0/16) value will provide 65,534 IPs for the cluster.
Each OpenShift node has its own subnet which allows to Pods to get an IP in that range. This variable configures number of bits to allocate to each host’s subnet.
OpenShift SDN Network Devices
· Bridge Network Device(br0): Bridge network interface that the pod containers will be attached to.
· Tunnel Interface: Tun0 is used for external network access. It is located port2 on br0. OpenShift SDN uses “netfilter” and routing rules to enable access to the external network via NAT.
· Vxlan: Vxlan provides access to container on remote nodes.
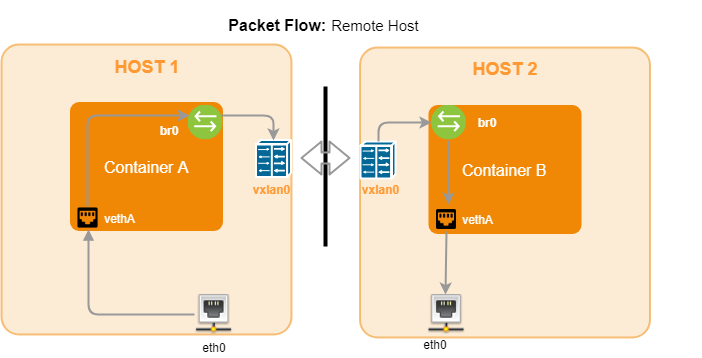
Basic Package Flow for OpenShift SDN
· Container A and B are located at same host

· Container A and B are working on same cluster but remote host.
· Container A connects to the external host

What is northbound interface / southbound interface? — Definition from WhatIs.com
OpenShift SDN — Networking | Architecture | OpenShift Container Platform 3.11